
Quantifying the Cost of Downtime: Why Robust IT Infrastructure Matters
Downtime can be a nightmare for any business, but it hits small businesses particularly hard. When systems go down, operations grind to a halt, and each passing minute can equate to lost revenue. This is why having a robust IT infrastructure is not a luxury, but a necessity.

ROI on Information Security: Is It Worth It for Small Businesses?
When running a small business, every investment counts. As entrepreneurs allocate resources to various parts of the business, questions often arise about the necessity and profitability of specific expenses. Among them, information security frequently becomes a point of discussion.

Anatomy of a Hack: A Detailed Breakdown of Notable Cyber Attacks
Information security threats are not only growing in number, but they are also becoming more sophisticated and damaging. While the impacts of these cyberattacks are often discussed, the detailed mechanics of how they actually unfold are frequently overlooked.

Unlocking the Power of Log Collection and SIEMs for Small Businesses
When it comes to securing the digital assets of a small business, log collection and Security Information and Event Management (SIEM) systems play a vital, yet often overlooked role. These powerful tools offer insight into your digital ecosystem's security, allowing you to detect, prevent, and respond to threats more effectively. This blog post will explore the importance of log collection and SIEMs, how they work, and why they're a must-have for small businesses navigating the modern cybersecurity landscape.

Navigating the Cybersecurity Landscape: The Critical Role of Incident Response
In today's digitally driven world, cybersecurity threats are an ever-present reality for organizations. As businesses become more interconnected and reliant on technology, the potential impact of these threats has grown exponentially. Given this landscape, being prepared to deal with cybersecurity incidents is no longer optional; it's an absolute necessity.

Understanding Advanced Persistent Threats: An In-Depth Look
When it comes to cyber threats, there are plenty to choose from - malware, ransomware, phishing attacks, and more. However, one type of threat is especially dangerous due to its stealthy nature and potentially devastating impact - the Advanced Persistent Threat (APT).

Optimizing IT Costs: Strategies for Effective IT Budgeting and Expense Management
As integral as IT is, managing its associated costs can be a complex endeavor. Small to mid-sized business owners may feel particularly challenged, balancing the need for robust IT infrastructure against budget constraints. Yet, with strategic planning and judicious management, it's possible to optimize IT costs without sacrificing performance. Let's explore some key strategies.

AI and Information Security: The Rising Concerns
As the artificial intelligence (AI) revolution continues to unfold, it's clear that AI technologies have immense potential to drive progress across sectors. However, this potential isn't limited to positive impacts. On the flip side, as AI becomes more integrated into our systems and processes, it introduces new vulnerabilities that can be exploited by cyber attackers.

The Importance of Disaster Recovery Planning: Ensuring Business Continuity
In a digital world, data has become the lifeblood of business operations. However, the same technology that empowers us can also be vulnerable to disruptions - from natural disasters and power outages to cyberattacks and human error. That's why having a robust disaster recovery plan is no longer optional for businesses, irrespective of their size. It is a key part of ensuring business continuity and mitigating risks associated with downtime. Here, we delve into the importance of disaster recovery planning and how it helps ensure business continuity.

Combating Phishing Attacks: The Essential Role of Employee Training
It's a well-established fact that cybersecurity threats are a top concern for organizations worldwide. Cyber attackers persistently seek to exploit weak points in systems, and there's no weak point more susceptible than the human element.
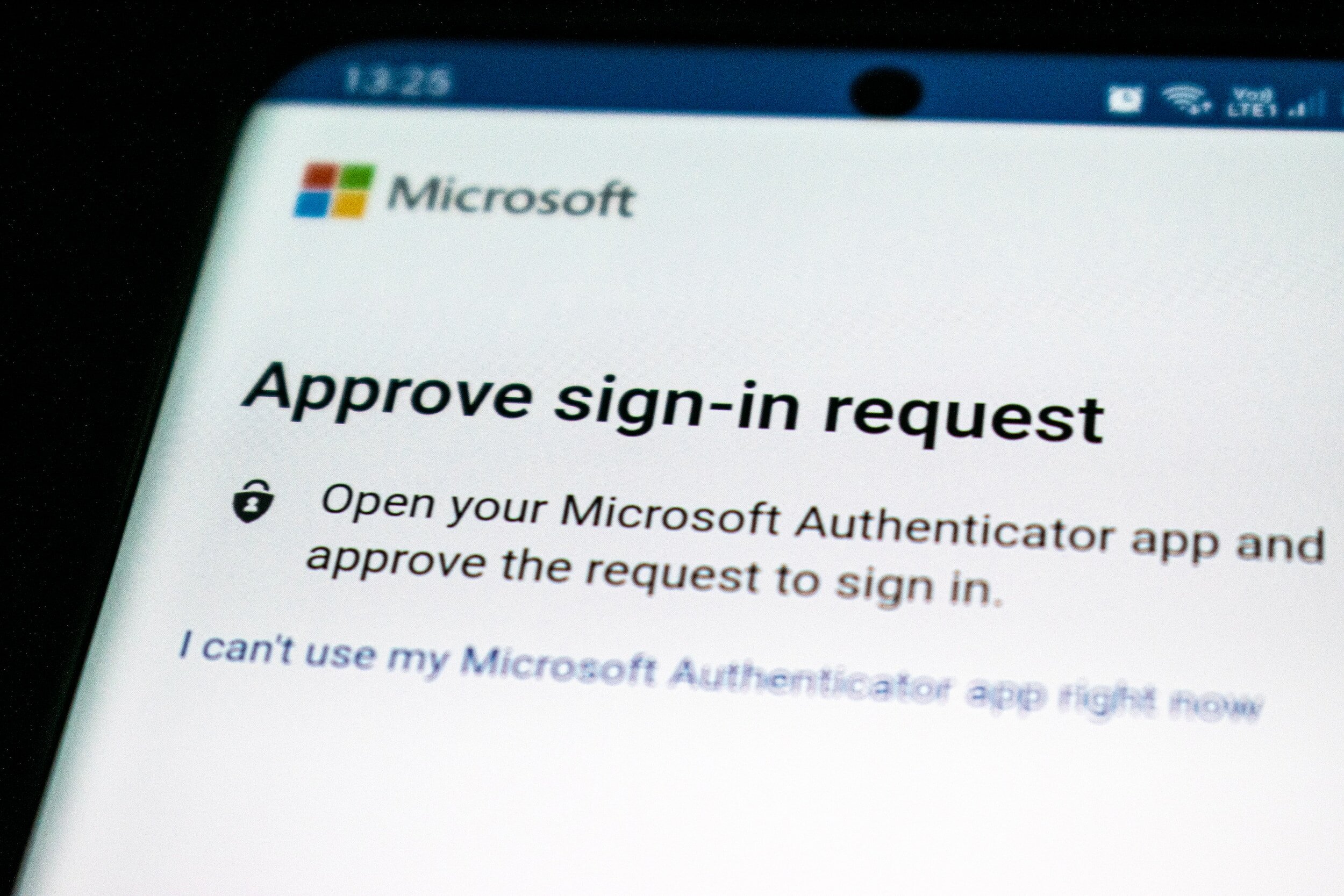
The Power of Multi-Factor Authentication: Elevating Your Security Posture
In the modern digital age, businesses of all sizes face an ever-evolving array of cybersecurity threats. While there's no silver bullet solution to guarantee absolute security, some measures can significantly reduce the risk of a breach. One such measure is multi-factor authentication (MFA), a simple yet powerful tool in the cybersecurity toolkit. In this blog post, we delve into what MFA is, how it works, and why it's a crucial component of a comprehensive security strategy.

Enhancing Your Cybersecurity Landscape with Microsoft Azure and Office 365
In the ever-evolving online realm, protecting your business's cyber environment is a critical task. Microsoft's Azure and Office 365 platforms offer a robust suite of tools and features that help safeguard your digital ecosystem against potential threats. This blog post will explore how you can leverage these tools to enhance your business's cybersecurity and why doing so is crucial.

The Top 5 Cybersecurity Best Practices Every Business Should Implement
Cybersecurity has become a pressing concern for businesses of all sizes. A single cyber attack can cause significant financial loss, damage brand reputation, and result in loss of critical data. Therefore, implementing robust cybersecurity measures is not just an option but a necessity. This post explores five cybersecurity best practices every small and medium-sized business should implement to safeguard their digital assets.
